CNAPP: The Unified Future of Cloud Security
Discover how CNAPP is revolutionizing cloud security in 2025—top trends, leading platforms, cloud risks, recent breaches, and what comes next.
CYBERSECURITY
TAOCS
5/29/20252 min read

📈 CNAPP Trends in 2025: Key Developments in Cloud-Native Security
The CNAPP market is growing rapidly, driven by demand for unified cloud security solutions.
🔍 Top CNAPP Trends:
1. Unified Cloud-Native Security
CNAPP platforms now combine:
CSPM
CWPP
CIEM
KSPM (Kubernetes Security Posture Management)
Shift-left security (DevSecOps)
This enables full-lifecycle protection—from infrastructure-as-code to production runtime.
As cloud adoption continues to skyrocket, security teams face increasing complexity, visibility gaps, and evolving threats. Traditional cloud security tools—like CSPM (Cloud Security Posture Management), CWPP (Cloud Workload Protection Platform), and CIEM (Cloud Infrastructure Entitlement Management)—each address different aspects of the cloud environment. But in silos, they fall short.
That’s where CNAPP (Cloud-Native Application Protection Platform) steps in. CNAPP unifies these disparate capabilities into a single, holistic cloud security platform, giving organizations the visibility, control, and context they need to secure cloud-native applications from code to runtime.
In this blog, we’ll explore what CNAPP is, why it matters in 2025, current trends, top CNAPP vendors, cloud attack surfaces, recent breaches, and what’s coming next.
2. Agentless and Context-Aware Scanning
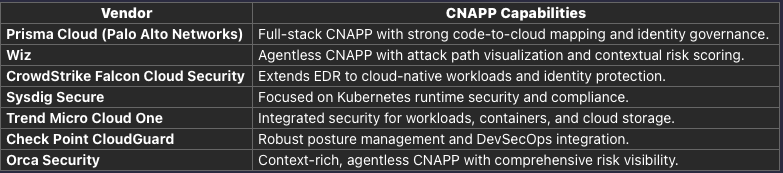
Platforms like Wiz and Orca Security leverage agentless deployment and graph-based analysis to correlate misconfigurations, vulnerabilities, identities, and network exposure.
3. AI-Driven Risk Prioritization
Modern CNAPPs apply machine learning and attack path analysis to reduce alert noise and surface the most critical threats based on context.
4. Cloud-Native Runtime Protection
CNAPPs are now providing behavioral analytics, drift detection, and real-time blocking of malicious activity inside workloads and containers.
5. DevSecOps Integration (Shift Left)
By embedding into CI/CD pipelines, CNAPPs help security teams:
Scan container images
Validate IaC templates
Flag secrets in code
Enforce policies before deployment
🔐 What is the CNAPP Architecture?
At its core, a CNAPP platform provides integrated visibility and protection across:
Cloud configurations (CSPM)
Workloads and containers (CWPP)
Identity and access entitlements (CIEM)
Kubernetes clusters (KSPM)
Code pipelines (Shift Left)
Runtime environments (EDR-like for the cloud)
This unified architecture reduces blind spots and allows for cloud-native threat detection, response, and remediation in real time.
🌩️ Cloud Threat Surface: New Attack Vectors in the Cloud
As cloud environments become more dynamic, the cloud attack surface continues to expand. CNAPPs aim to address threats like:
🚨 Top Cloud Security Risks:
Misconfigured storage buckets (e.g., public S3)
Overprivileged IAM roles
Unpatched containers or VMs
Exposed APIs
Shadow IT and ephemeral resources
Vulnerable infrastructure-as-code deployments
A 2024 Gartner report states that 75% of cloud security failures will result from misconfigurations, not cloud provider faults.
🧨 Recent Cloud Security Breaches You Should Know
Understanding recent cloud breaches helps underscore why CNAPP capabilities are essential:
1. Commvault Breach (May 2025)
Commvault’s SaaS backup platform was compromised via a misconfigured public endpoint. Customer metadata and access logs were exposed, triggering widespread alerts from security agencies.
2. Microsoft Azure AD Token Exploit
Attackers forged OAuth tokens to exploit flaws in Azure AD authentication, enabling cross-tenant access and lateral movement—showcasing identity risks in the cloud.
3. CapitalOne-style SSRF Redux
A modern variation of the 2019 CapitalOne breach emerged, using server-side request forgery (SSRF) to access internal metadata APIs in cloud instances, highlighting persistent architectural risks.
CNAPP Is the Future—but Not the Final Destination
CNAPP represents a new security paradigm—one that aligns with how cloud-native applications are built, deployed, and operated. It promises better visibility, integrated protection, and faster response across the entire cloud environment.
But here's the twist…
As CNAPP becomes the new security perimeter—are adversaries already adapting to bypass it?
In our next post, we’ll dive into the emerging threat techniques aimed at CNAPP-aware environments—and how security teams can get ahead of the curve with adaptive defense strategies.
Subscribe newsletter